There are generally three different ways to approach hacking a target:
Hacking the encryption (cryptography)
This is very difficult, and time/computing power-intensive, as the algorithms we use are generally very hard to crack. Quantum computing, if cheaply and easily available, could present issues, but right now isn't at a point where it's a huge threat.
The best way to protect against this is to ensure that you're using difficult to break encryption algorithms, and that you're implementing them correctly. For example, SHA-0, SHA-1, DES, and MD5 are generally considered to be insecure and therefore shouldn't be used. For more details on using secure algorithms, check out this post on cryptography. Don't write your own encryption algorithms. You're unlikely to successfully create better algorithms than the current standards.
Hacking the software/hardware that was used to perform the encryption.
This is easier — a lot of software is written by developers who don't know how to code securely (and writing secure code is HARD). People make mistakes and it only takes one mistake for software to have a bug (and sometimes it doesn't even need to be a mistake - some vulnerabilities are caused by new ways of exploiting computer and software design, like Spectre). Both hardware and software generally have a lot of vulnerabilities.
However, this is more useful if you have a specific target (if, for example, you wanted to hack a specific piece of software or hardware and are interested in expending a lot of time to find and exploit a vulnerability). This is made easier by people who search for vulnerabilities, publicize them, or sell them.
But, if you are a government agency and the goal is to surveil everything, you probably need a backdoor into the hardware or software. Backdoors essentially mean planned holes in the code that intentionally allow someone to bypass the encryption to access the information it protects. The problem with backdoors is that if they exist, the software can never be truly secure, because there’s always the possibility that someone more nefarious could find the backdoor.
It's almost impossible to be entirely secure, and even if your code is perfectly secure, you're probably also leveraging code created by third parties (and those folks are using code created by fourth parties, who are using code created by fifth parties, and so on) or open source code/repositories. It's essentially impossible to only use perfectly secure software and hardware - or even to know if what you're using is secure, unless you're building absolutely everything yourself (which is cost-prohibitive and unlikely to be successful since most companies do not hire specialists in every step of their supply chain).
However, static and dynamic code scanning, as well as training programs for developers, can help catch vulnerabilities in code before it goes to production. Additionally, Security Champions programs, where developers work closely with application security teams to understand and mitigate security issues, can also aid in mitigation. Finally, programs like bug bounties and penetration tests can leverage white hat hackers to help identify problems with your systems before more nefarious hackers find them.
If you're interested in legal hacking, bug bounties can be a great way to get some practice, improve your skills, show potential employers that you're interested in security, and potentially make some money (however, I wouldn't depend on this as a source of income - very few hackers on bug bounty platforms make very much money).
Social Engineering.
This essentially means tricking people. You don’t have to hack anything if you can convince someone to click on a phishing email or just tell you their password (that’s probably easier anyway).
Give a man an 0day and he'll have access for a day, teach a man to phish and he'll have access for life.
— thaddeus e. grugq (@thegrugq) February 7, 2015
Often user awareness isn’t the sexiest part of security, but it is important. The Verizon Data Breach Report estimated that 93% of all breaches globally in 2018 began with a phishing or pretexting attack.
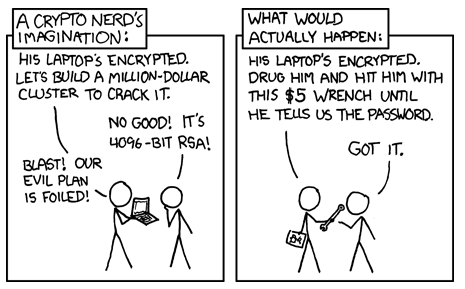
This is really, really difficult to protect against. The best option is a layered defense. This means protections against each potential part of the attack. For example:
- Implementing comprehensive email filtering to filter out as many spam and phishing emails as possible, before they reach your users.
- Using measures like DKIM, DMARC, and SPF to enhance your email protections.
- Blocking traffic to known malicious or suspicious sites via proxies to prevent users from being able to access and download potential payloads.
- Using anti-virus and endpoint protection tools on every system. These tools can help prevent payloads from running, or can monitor and detect unusual behavior and alert a security team who can investigate.
- Patching systems regularly to prevent exploits from being able to run.
- Requiring security training for all employees at least annually in order to educate them about the dangers of phishing and social engineering attacks.
- Having a simple process for users to report phishing emails, calls, social media requests, etc. Make it easy for them - publicize how to contact the security team widely, and understand that if it takes more than a few clicks, they'll probably give up (my rule is if it takes more than 3 clicks, people won't do it). Then, make sure people feel comfortable doing so, and have a good experience when they do. If they don't, you'll probably see less reports in the future.


